Table of Contents
Enhancing Switch Security
These blog posts I created to help me as a reference tool, as well as a way of retaining the knowledge. If you find it useful that’s just a plus.
Switches are critical components in any network, connecting multiple devices and managing data traffic between them. However, without proper security measures, switches can become vulnerable to attacks, such as unauthorized access, MAC flooding, and VLAN hopping. Enhancing switch security involves configuring various features to protect the switch and the network it supports.
Configuration Commands
Line Consol 0
Accesses console line configuration mode, allowing you to set up security for console access.
Syntax:
line console 0
Example:
Router1>enable
Router1#configure terminal
Router1(config)#line console 0
Line VTY 0 15
Enters configuration mode for virtual terminal (Telnet) lines, allowing you to configure remote access security.
Syntax:
line vty 0 15
Example:
Router1>enable
Router1#configure terminal
Router1(config)#line vty 0 15
Login
Enables password checking at login, requiring a password before accessing the switch via console or Telnet.
Syntax:
login
Example:
Router1>enable
Router1#configure terminal
Router1(config)#line vty 0 4
Router1(config-line)#login
Password
Specifies the password required for accessing the switch via the console or Telnet.
Syntax:
password [password]
Example:
Router1>enable
Router1#configure terminal
Router1(config)#line vty 0 4
Router1(config-line)#password p4ssw0rd!
Enable Secret
Sets the enable secret password, which provides access to privileged EXEC mode. The password is stored in an encrypted format.
Syntax:
enable secret [password]
Example:
Router1>enable
Router1#configure terminal
Router1(config)#enable secret p4ssw0rd!
Port Security Commands
These commands enhance security at the port level by controlling MAC addresses and preventing unauthorized devices from accessing the network.
Switchport Port-Security
Enables port security on a switch interface, allowing you to control which MAC addresses can access the network through that port.
Syntax:
switchport port-security
Example:
Router1>enable
Router1#configure terminal
Router1(config)#interface GigabitEthernet0/1
Router1(config-if)#switchport port-security
Switchport Port-Security Violation
Sets the violation mode for port security, determining the action to take if an unauthorized device tries to access the network.
Syntax:
switchport port-security violation [protect | restrict | shutdown]
protect: Drops packets with unknown source MAC addresses.restrict: Drops packets and generates an SNMP trap.shutdown: Shuts down the port if a violation occurs.
Example:
Router1>enable
Router1#configure terminal
Router1(config)#interface GigabitEthernet0/1
Router1(config-if)#switchport port-security violation restrict
Password and Encryption
Service Password-Encryption
Encrypts all current and future passwords configured on the switch, providing an additional layer of security.
Syntax:
service password-encryption
Example:
Router1>enable
Router1#configure terminal
Router1(config)#service password-encryption
Banner Login
Configures a message that is displayed at user login attempts, often used to display security warnings or legal notices.
Syntax:
banner login #[message]#
Example:
Router1>enable
Router1#configure terminal
Router1(config)#banner login #Only the weak shall perish#
Verification and Management
Show Mac-Address-Table
Displays the Media Access Control (MAC) forwarding table, allowing you to verify which MAC addresses are associated with which ports.
Syntax:
show mac-address-table
Example:
Router1>enable
Router1#show mac-address-table
Show Running-Config
Displays the active configuration file, allowing you to verify password settings, port security configurations, and other security-related configurations.
Syntax:
show running-config
Example:
Router1>enable
Router1#show running-config
EVE-NG Lab
This lab aims to provide hands-on experience in configuring various switch security features on Cisco switches using EVE-NG. You will learn how to:
- Configure Port Security to restrict access based on MAC addresses.
- Disable unused ports to minimize potential attack vectors.
- Enable BPDU Guard to protect against rogue switches.
- Configure Storm Control to prevent broadcast storms.
- Enable DHCP Snooping to prevent rogue DHCP servers.
- Configure Dynamic ARP Inspection (DAI) to prevent ARP spoofing attacks.
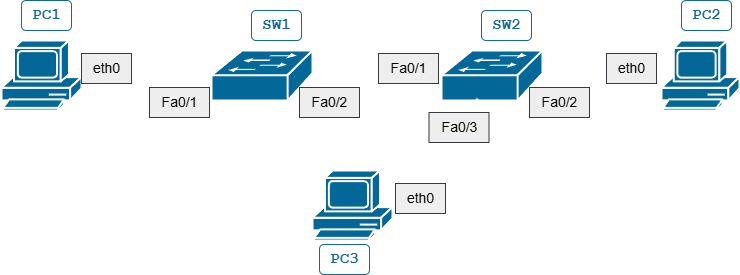
Basic Settings
Configure Hostname and Disable Unused Ports
Switch 1
Switch>enable
Switch#configure terminal
Switch(config)#hostname SW1
SW1(config)#interface range FastEthernet 0/3 - 24
SW1(config-if-range)#shutdown
SW1(config-if-range)#exit
SW1#write memory
interface range : Will configure ports FastEthernet 0/3 – 24.shutdown : Will shutdown all those ports.write memory : Saves configuration.
Switch 2
Switch>enable
Switch#configure terminal
Switch(config)#hostname SW2
SW2(config)#interface range FastEthernet 0/4 - 24
SW2(config-if-range)#shutdown
SW2(config-if-range)#exit
SW2#write memory
interface range: Will configure ports FastEthernet 0/4 – 24.shutdown: Will shutdown all those ports.write memory: Saves configuration.
Port Security
Configure Port Security on Switch 1
Port FA0/1
SW1>enable
SW1#configure terminal
SW1(config)#interface FastEthernet 0/1
SW1(config-if)#switchport mode access
SW1(config-if)#switchport port-security
SW1(config-if)#switchport portsecurity maximum 2
SW1(config-if)#switchport port-security mac-address sticky
SW1(config-if)#switchport port-securty violation shutdown
SW1(config-if)#exit
SW1(config)#exit
SW1#write memory
switchport mode access: Forces the port into access mode, suitable for connecting end devices.switchport port-security: Enables port security on the interface.switchport port-security maximum 2: Allows only two MAC addresses on this port.switchport port-security mac-address sticky: Learns MAC addresses dynamically and adds them to the running configuration.switchport port-security violation shutdown: Shuts down the port if a violation occurs.
Verify Port Security
Display port security details:
SW1>enable
SW1#show port-security interface FastEthernet 0/1
Expected Output:
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Maximum MAC Addresses : 2
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 1
Last Source Address : 0000.aaaa.bbbb
Test Port Security
Connect an unauthorized device to Fa0/1 and observe that the port goes into error-disabled state.
SW1>enable
SW1#show interface FastEthernet 0/1 status
Expected Output:
Fa0/1 err-disabled
Recovering from Violation
Configure the IP address for S0/0/1 interface:
SW1>enable
SW1#configure terminal
SW1(config)#interface FastEthernet 0/1
SW1(config-if)#shutdown
SW1(config-if)#no shutdown
Expected Output:
Interface Fa0/1 changed state to down
Interface Fa0/1 changed state to up
Port Security on Switch 2
Port Fa0/2 and Fa0/3
SW1>enable
SW1#configure terminal
SW1(config)#interface FastEthernet 0/2 - 3
SW1(config-if)#switchport mode access
SW1(config-if)#switchport port-security
SW1(config-if)#switchport portsecurity maximum 2
SW1(config-if)#switchport port-security mac-address sticky
SW1(config-if)#switchport port-securty violation shutdown
SW1(config-if)#exit
SW1(config)#exit
SW1#write memory
switchport mode access: Forces the port into access mode, suitable for connecting end devices.switchport port-security: Enables port security on the interface.switchport port-security maximum 2: Allows only two MAC addresses on this port.switchport port-security mac-address sticky: Learns MAC addresses dynamically and adds them to the running configuration.switchport port-security violation shutdown: Shuts down the port if a violation occurs.
BPDU Guard and Portfast
Protect the network from potential loops caused by the addition of unauthorized switches by disabling ports that receive unexpected BPDUs
Enable BPDU Guard and PortFast
Switch 1
SW1>enable
SW1#configure terminal
SW1(config)#spanning-tree portfast bpduguard default
SW1(config)#interface FastEthernet 0/1
SW1(config-if)#spanning-tree portfast
SW1(config-if)#exit
spanning-tree portfast bpduguard default: enables BPDU Guard on all PortFast-enabled ports. If a BPDU is received on these ports, the port is disabled to prevent potential loops.spanning-tree portfast: Enables portfast on the interface.
Switch 2
SW2>enable
SW2#configure terminal
SW2(config)#spanning-tree portfast bpduguard default
SW2(config)#interface FastEthernet 0/2 - 3
SW2(config-if)#spanning-tree portfast
SW2(config-if)#exit
spanning-tree portfast bpduguard default: enables BPDU Guard on all PortFast-enabled ports. If a BPDU is received on these ports, the port is disabled to prevent potential loops.spanning-tree portfast: Enables portfast on the interface.
Storm Control
Configure Storm Control on Switch 1
Port FA0/1
SW1>enable
SW1#configure terminal
SW1(config)#interface FastEthernet 0/1
SW1(config-if)#storm-control broadcast level 10.00
SW1(config-if)#storm-control multicast level 10.00
SW1(config-if)#storm-control unicast level 10.00
SW1(config-if)#storm-control action shutdown
storm-control broadcast level 10.00: Limits broadcast traffic to 10% of the interface’s bandwidth.storm-control action shutdown: Shuts down the interface if the storm control threshold is exceeded.
Display Storm Control Settings
SW1>enable
SW1#show storm-control interface FastEthernet 0/1
Expected Output:
Interface Fa0/1
Broadcast level 10.00%
Multicast level 10.00%
Unicast level 10.00%
Action: Shutdown
DHCP Snooping
Configure DHCP Snooping on Switch 2
Enable Globally
SW2>enable
SW2#configure terminal
SW2(config)#ip dhcp snooping
SW2(config)#ip dhcp snooping vlan 1
SW2(config)#interface FastEthernet 0/1
SW2(config-if)#ip dhcp snooping trust
SW2(config-if)#exit
Verify DHCP Snooping Settings:
SW2>enable
SW2#show ip dhcp snooping
Expected Output:
DHCP Snooping is enabled
DHCP Snooping is configured on following VLANs:
1
Operation mode: VLAN
DHCP Snooping is configured on the following Interfaces:
Trusted Interfaces:
FastEthernet0/1
Untrusted Interfaces:
FastEthernet0/2
FastEthernet0/3
Dynamic ARP Inspection (DAI)
Configure DAI on Switch 2
Enable DAI for VLANs
SW2>enable
SW2#configure terminal
SW2(config)#ip arp inspection vlan 1
SW2(config)#interface FastEthernet 0/1
SW2(config-if)#ip arp inspection trust
SW2(config-if)#exit
Verify DAI Settings:
SW2>enable
SW2#show ip arp inspection
Expected Output:
Interface Trust State Rate (pps)
------------ ----------- ----------
Fa0/1 Trusted Unlimited
Fa0/2 Untrusted 15
Fa0/3 Untrusted 15
